AI security protects artificial intelligence systems from attacks while using AI technologies to strengthen cybersecurity defenses.
Organizations worldwide are discovering that AI systems face unique threats that traditional cybersecurity cannot address. These intelligent systems process vast amounts of data and make autonomous decisions, creating new opportunities for attackers to exploit vulnerabilities. At the same time, AI technologies offer powerful capabilities for detecting and responding to cyber threats faster than human analysts ever could.
The stakes have never been higher for getting AI security right. A single compromised AI model could expose sensitive customer data, manipulate business decisions, or disrupt critical operations across entire organizations. The complexity of AI algorithms makes it difficult to predict how systems will behave under attack, while the speed of AI adoption often outpaces security implementations.
The landscape of AI security continues to evolve rapidly as both defenders and attackers develop more sophisticated techniques. Understanding the fundamentals of AI security has become essential for organizations seeking to harness AI benefits while protecting against emerging threats.
What is AI Security
AI security refers to protecting artificial intelligence systems from threats while using AI technologies to enhance cybersecurity defenses. This dual approach addresses both defending AI systems from attacks and leveraging AI capabilities to strengthen overall security postures.
Traditional cybersecurity focuses on protecting static systems and data from external threats. AI security deals with dynamic systems that continuously learn and make autonomous decisions. These systems process massive datasets and adapt their behavior based on new information, creating attack surfaces that don’t exist in conventional software.
The Two Sides of AI Security
AI-Powered Cybersecurity uses machine learning algorithms to detect patterns in network traffic that indicate potential threats. These systems analyze security logs to identify suspicious activities and establish baselines for normal user behavior. When anomalies occur, AI systems can flag them for investigation and even automate certain response procedures.
Protecting AI Systems involves securing training data against corruption and implementing access controls to prevent unauthorized modifications. Organizations monitor AI outputs for signs of manipulation and protect proprietary algorithms from theft. This protection extends across the entire AI lifecycle from development through deployment and ongoing operation.
The interconnected nature of these approaches means vulnerabilities in AI-powered security tools can compromise overall cybersecurity. Inadequate protection of AI systems can undermine their effectiveness as security tools, creating cascading risks across organizational technology environments.
Types of AI Security Threats

Source: SecurDI
AI systems face four primary categories of security threats that differ significantly from traditional cybersecurity risks:
Data Poisoning Attacks
Data poisoning occurs when attackers deliberately introduce corrupted information into datasets used to train AI models. Since training data forms the foundation of how AI systems learn, contaminated data can fundamentally alter system behavior.
Attackers typically introduce poisoned data gradually to avoid detection. Small changes to existing data points or carefully crafted false information can slowly shift model behavior over time. A compromised medical AI system might begin misclassifying symptoms, while a fraud detection system could start approving suspicious transactions.
Adversarial Machine Learning
Adversarial attacks involve creating specially designed inputs that cause AI systems to make incorrect predictions. These inputs appear normal to humans but contain subtle modifications that exploit weaknesses in AI algorithms.
Research has shown that adding barely visible noise to a photograph of a panda can cause an AI system to identify it as a gibbon. Small stickers placed on stop signs have caused autonomous vehicle systems to misinterpret them as speed limit signs. These attacks work because AI systems process information differently than humans do.
Model Theft and Extraction
Model theft attacks involve stealing AI models or extracting sensitive information they contain. Attackers repeatedly query AI systems and analyze outputs to reverse-engineer proprietary algorithms. This theft can cost organizations millions in lost competitive advantage and research investment.
Model inversion attacks attempt to reconstruct training data from AI outputs. By analyzing how models respond to different inputs, attackers can potentially extract recognizable faces from facial recognition systems or sensitive medical information from healthcare AI models.
AI-Enhanced Cyberattacks
Generative AI enables attackers to create realistic phishing emails, fake websites, and convincing social media profiles at unprecedented scale. Voice cloning technology allows attackers to impersonate trusted individuals in phone-based social engineering schemes.
Machine learning algorithms help malware adapt to security defenses and automatically modify code to evade detection systems. Deepfake technology creates realistic but fake videos or audio recordings that can spread misinformation or damage reputations.
Why AI Security Matters for Organizations
AI security failures can disrupt core business operations in ways traditional security breaches cannot. When AI systems that automate critical processes become compromised, organizations may lose the ability to make accurate decisions or maintain operational continuity.
Manufacturing companies using AI for quality control face production shutdowns if their systems begin misclassifying defective products. Financial institutions relying on AI for fraud detection could suffer losses if their models start approving fraudulent transactions. Healthcare organizations risk patient safety if their diagnostic AI provides incorrect recommendations.
Business Risk Implications
The integrity of AI-driven decision-making becomes questionable once security is compromised. Unlike traditional systems where failures are often immediately apparent, AI security breaches can manifest as gradual performance degradation that resembles normal operational variations.
Reliability concerns extend beyond immediate operational impacts to long-term business relationships. Customers who lose trust in AI-powered services may switch to competitors, while partners may terminate relationships with organizations that cannot guarantee AI system security.
Data breaches involving AI systems often have amplified consequences because AI models can reveal patterns in data that weren’t apparent in original datasets. Personal information that seemed anonymized may become identifiable when processed through compromised AI systems.
Regulatory and Compliance Requirements
The European Union AI Act establishes risk-based requirements that vary according to how AI systems are classified. High-risk applications face stringent security and governance mandates that organizations must meet to remain compliant.
Organizations using AI in healthcare, finance, transportation, and other regulated industries navigate complex regulatory landscapes. The NIST AI Risk Management Framework provides structured approaches for managing AI-related risks while ensuring regulatory compliance.
Cross-border operations create additional compliance complexity as organizations satisfy AI governance requirements in multiple jurisdictions simultaneously. Documentation requirements often extend beyond traditional software systems to include detailed records of training data and model development processes.
AI Security vs Traditional Cybersecurity

Source: ResearchGate
AI security differs fundamentally from traditional cybersecurity in scope, complexity, and threat vectors. Traditional cybersecurity protects static systems using signature-based detection and rule-based controls. AI security requires probabilistic approaches that account for unpredictable machine learning behaviors.
Key Differences
- Attack Targets: Traditional attacks focus on databases and networks; AI attacks target training data and models
- Vulnerability Sources: Code flaws versus algorithm weaknesses and biased training data
- Attack Persistence: Temporary system compromise versus permanent model corruption
- Detection Methods: Signature-based versus behavioral analysis and statistical anomaly detection
- Recovery Process: System restoration versus model retraining and data validation
The “black box” problem in AI creates complexity where security teams cannot fully understand how systems reach decisions. This opacity makes it difficult to predict or prevent security failures using traditional methods.
Data dependency represents the most significant vulnerability in AI systems. Unlike traditional software that processes data according to predetermined rules, AI systems derive behavior from training data patterns. Attackers exploit this dependency through data poisoning attacks that permanently alter model behavior.
AI Security Best Practices
Securing AI systems requires comprehensive approaches that address unique vulnerabilities throughout the AI lifecycle. Organizations face distinct challenges protecting AI systems because traditional cybersecurity measures often prove insufficient.
Security by Design Principles
Security by design integrates protective measures from the earliest stages of AI development rather than adding security after deployment. Development teams incorporate threat modeling during initial design to identify potential attack vectors and vulnerabilities.
- Controlled Environments: Establish separated spaces for training AI models away from production systems
- Version Control: Implement tracking systems for model management and change documentation
- Security Reviews: Conduct assessments at each development milestone before progression
- Data Validation: Verify integrity and authenticity of training datasets before model development
Secure development practices include maintaining separation between development, testing, and production environments. Teams implement checksums, digital signatures, and provenance tracking to detect potential data poisoning attempts.
Continuous Monitoring and Detection
Real-time monitoring systems track AI performance and behavior to identify anomalies indicating security threats. These capabilities extend beyond traditional network monitoring to include AI-specific metrics and behavioral patterns.
Behavioral analysis tools establish baseline performance metrics for AI models and alert security teams when outputs deviate significantly from expected patterns. Input validation monitoring examines data flowing into AI systems to identify potentially malicious or adversarial inputs.
Model drift detection identifies when AI systems begin producing different outputs over time, which may indicate data quality issues or potential security compromises. Comprehensive logging captures detailed records of AI system interactions for forensic analysis following security incidents.
Access Controls and Authentication
AI systems require specialized access control mechanisms protecting both models and sensitive training data. Role-based access control systems limit user permissions based on job responsibilities and operational requirements.
Multi-factor authentication secures access to AI development environments, training datasets, and production systems. API security controls protect interfaces between AI systems and other applications through authentication tokens and rate limiting.
Data access permissions restrict who can view, modify, or use training datasets and operational data. Organizations establish approval workflows for model deployment and maintain audit trails of all access and modification activities.
AI Security Frameworks and Standards
Organizations rely on established frameworks to guide AI security implementations. These guidelines provide structured approaches for managing AI-related risks while ensuring consistent security practices across industries.
NIST AI Risk Management Framework
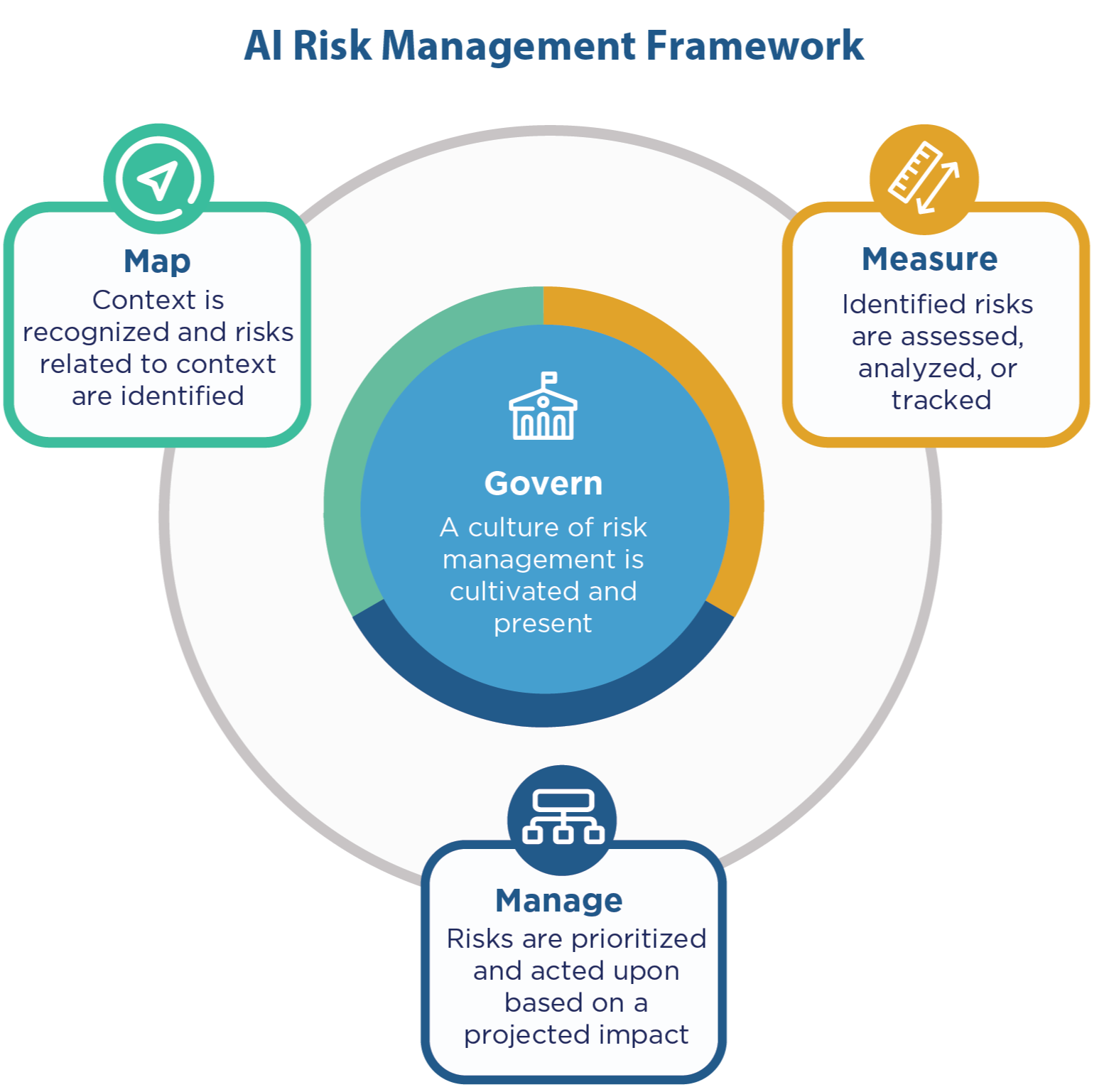
Source: NIST AI Resource Center
The National Institute of Standards and Technology provides systematic methodologies for identifying, assessing, and mitigating AI risks throughout system lifecycles. Released in January 2023, the framework organizes activities into four core functions.
The Govern function establishes organizational structures prioritizing risk awareness and accountability. Organizations implementing this function create formal risk management processes and define roles for AI oversight while ensuring compliance with legal requirements.
The Map function helps organizations understand AI systems within broader operational contexts. Teams identify potential impacts across technical and social dimensions while documenting data flows through AI systems and assessing positive and negative impacts.
The Measure function addresses risk assessment through quantitative and qualitative approaches. Organizations conduct impact assessments, employ diverse risk evaluation techniques, and develop metrics for monitoring AI performance and security.
The Manage function guides organizations in prioritizing identified risks through technical controls and procedural safeguards. Implementation involves developing response strategies, establishing incident management procedures, and creating continuous monitoring processes.
ISO AI Security Standards
The International Organization for Standardization has developed comprehensive standards addressing AI security and governance requirements. ISO/IEC 42001:2023 provides foundational frameworks for AI management systems with structured risk assessment methods.
The standard establishes formal requirements for AI governance, including mandatory risk assessment procedures and control implementation protocols. Organizations implement threat modeling methodologies such as STRIDE to analyze AI system vulnerabilities systematically.
ISO/IEC 42001:2023 integrates with existing information security management systems while addressing AI-specific requirements. Organizations leverage current ISO 27001 implementations as foundations for AI security management systems.
Industry-Specific Guidelines
Healthcare organizations follow specialized guidelines addressing HIPAA compliance requirements and patient safety considerations. Medical AI applications require additional authentication measures for systems accessing patient data and audit trails for AI-assisted clinical decisions.
Financial services organizations operate under strict regulatory oversight extending to AI system security. The Federal Financial Institutions provides guidance emphasizing model risk management and consumer protection for banking AI applications.
Government and public sector organizations follow specialized guidelines addressing transparency and accountability considerations. The Office of Management and Budget has issued memoranda requiring federal agencies to implement specific AI governance and security measures.
How to Implement AI Security in Your Organization
Organizations implementing AI security face unique challenges requiring systematic approaches. The implementation process involves assessment and planning, roadmap development, and team building phases.
Assessment and Planning Phase
Implementation begins with cataloging all AI systems within the organization. This inventory includes production systems, development environments, third-party AI services, and experimental projects. Teams document purpose, data sources, decision-making scope, and integration points for each system.
Risk assessment evaluates potential threats across technical, operational, and governance dimensions. Technical risks include model vulnerabilities and data poisoning attacks. Operational risks encompass supply chain dependencies and access control weaknesses.
Current security controls receive evaluation against AI-specific requirements. Traditional cybersecurity measures may not address AI vulnerabilities effectively, requiring identification of gaps where existing controls fail.
Implementation Roadmap

Source: SlideGeeks
Implementation proceeds through four phases building security capabilities progressively:
- Phase One: Establish foundational controls including access management and basic monitoring
- Phase Two: Introduce technical security measures targeting AI-specific vulnerabilities
- Phase Three: Expand monitoring capabilities through specialized AI environment tools
- Phase Four: Develop advanced capabilities including automated threat detection
Prioritization strategies guide resource allocation across implementation phases. High-risk AI systems processing sensitive data or making critical business decisions receive priority attention.
Resource planning addresses budget, personnel, and technology requirements across all phases. Organizations estimate costs for security tools, training programs, and additional staffing while considering timeline constraints.
Team Building and Training
AI security requires specialized expertise combining cybersecurity knowledge with understanding of AI technologies. Organizations typically establish dedicated AI security roles or expand existing security team responsibilities.
Core team composition includes security analysts with AI knowledge, data scientists with security awareness, and governance specialists understanding AI risk management. Cross-functional collaboration connects teams with development groups and business units.
Training programs address different skill levels and role requirements. Technical personnel receive instruction on AI security tools and threat detection methods. Business stakeholders learn about AI risk management principles and governance requirements.
Frequently Asked Questions About AI Security
How much does implementing AI security typically cost for mid-sized organizations?
![]()
Source: Market.us
AI security costs typically represent 5 to 15 percent of total cybersecurity spending for organizations with significant AI deployments. Mid-sized organizations can expect initial implementation costs ranging from $50,000 to $200,000 depending on AI system complexity and existing security infrastructure.
Budget considerations include technology costs for specialized AI security tools, personnel expenses for security professionals with AI expertise, and ongoing operational costs for monitoring. Organizations often start with basic security measures and incrementally increase spending as AI adoption expands.
Financial services and healthcare organizations typically spend at the higher end due to regulatory requirements and sensitive data handling obligations.
What timeline should organizations expect for establishing basic AI security measures?
Organizations can establish foundational AI security measures within three to six months by focusing on access controls, basic monitoring, and policy development. This initial phase involves conducting risk assessments, implementing governance frameworks, and establishing security procedures for existing AI systems.
Full program maturity requires 12 to 24 months as organizations develop comprehensive capabilities across all security domains. The extended timeline reflects complexity of integrating AI security with existing cybersecurity programs and training personnel on AI-specific threats.
Implementation timelines vary based on current security maturity, AI deployment complexity, and available resources. Organizations with established cybersecurity programs can accelerate implementation by building upon existing capabilities.
Which specific metrics indicate whether an AI security program is working effectively?

Source: SideChannel
Threat detection rates provide quantitative measures of how effectively security systems identify AI-specific attacks like adversarial inputs and data poisoning attempts. Organizations track detection accuracy, false positive rates, and response times across different attack categories.
Incident response metrics measure response speed and effectiveness including mean time to detection, containment, and recovery for AI security incidents. Organizations also track the number and severity of incidents to identify trends and improvement opportunities.
Model performance stability indicates security program effectiveness through consistent AI system outputs over time. Significant performance variations may indicate security compromises or inadequate monitoring capabilities.
Compliance audit results offer external validation through independent assessments of policies, procedures, and technical controls. Organizations track audit findings, remediation timelines, and repeat issues to gauge continuous improvement efforts.
Building Your AI Security Strategy
Creating effective AI security strategy requires organizations to think beyond traditional cybersecurity approaches. AI systems introduce unique vulnerabilities through their reliance on training data, complex algorithms, and continuous learning processes.
The foundation begins with understanding your organization’s specific AI risk profile. Different industries face distinct threats — healthcare organizations worry about patient data exposure through model inversion attacks, while financial institutions focus on adversarial attacks manipulating fraud detection systems.
Long-term success depends on building security considerations into every AI development stage rather than adding protections afterward. Organizations integrating security from initial planning through deployment and ongoing operations create more resilient systems.
Governance frameworks provide structure for consistent security practices across multiple AI initiatives. Organizations implementing comprehensive governance establish clear accountability, identify potential impacts, assess risks, and develop mitigation strategies that scale across their AI portfolio.


